Access via JUMPHOST SSH
Access to internal Linux workstations is also available through an SSH Jump Host: jump.fbk.eu using key-based authentication.
To access the service, you must send your public SSH key as an email attachment to [email protected], indicating the following in the subject line: "SSH via jump host access request". The key must be in openssh format, and the file must be named: <fbk_login_name>.pub. The same key should be inserted into ~/.ssh/authorized_keys of the destination PC to avoid further password prompts. SSH-DSS (DSA) keys are not supported due to their weakness. For maximum compatibility and security, use ed25519 keys.
Linux/Unix/Mac openssh
From Windows 10 1803 onwards, openssh is installed by default. For versions prior to Windows 10 1803, it must be installed. The .ssh configuration directory is located in $ENV:HOMEPATH/ for PowerShell or %HOMEPATH% for cmd. See config_jump_w10 as an example of a Windows ssh configuration file.
To access <hostname>.fbk.eu using your default public key (usually id_rsa.pub), the ssh command is:
ssh -J <fbk_login_name>@jump.fbk.eu <fbk_login_nam>@<hostname>.fbk.eu
second line
To use a different ssh key (jump_key), the command syntax is:
A more flexible solution is to create a separate configuration file, config_jump:
#
# Define the jumphost
#
Host fbkjumphost
Hostname jump.fbk.eu
User <fbk_login_name>
#
# Specify a non default private key
#
IdentityFile ~/.ssh/private_key_file
#
# Match all host except jumphost
#
Host * !fbkjumphost
Hostname %h
#
# Force user name
#
User <fbk_login_name>
#
# Specify a non default private key
#
IdentityFile ~/.ssh/private_key_file
Proxy fbkjumphost to be used in the command with
ssh -F config_jump <hostname>.fbk.eu</hostname>
NB: -J, -o, -F must precede any other option
Linux/Unix/Mac/Windows10 scp
The syntax for copying via ssh (Secure Copy) with the default key is:
scp -o ProxyJump=<fbk_login_name>@jump.fbk.eu local_patch <fbk_login_name>@<hostname>.fbk.eu:remote_path
while with a separate public key, the command becomes:
scp -o ProxyCommand="ssh -i ~/.ssh/jump_key -W %h:22 <fbk_login_name>@jump.fbk.eu" - i~/.ssh/jump_key local_path <fbk_login_name>@<hostname>.fbk.eu:remote_path local_path
Simpler is copying config_jump via the configuration file:
scp -F config_jump local_path <fbk_login_name>@<hostname>.fbk.eu:remote_path
NB: -o, -F devono precedere ogni altra opzione
Linux/Unix/Mac/Windows10 rsync
To use remote sync with the default key, you must add the following to the rsync command:
--rsh "ssh -J <fbk_login_name>@jump.fbk.eu -l <fbk_login_name>"
To use the remote sync with a different key:
--rsh "ssh -o ProxyCommand='ssh -i ~/.ssh/jump_key -W %h:22 <fbk_login_name>@jump.fbk.eu' - i ~/.ssh/jump_key -l <fbk_login_name>"
Remote sync with a configuration file requires adding the following to the rsync command:
--rsh "ssh -F config_jump"
Linux/Mac/Windows SSH key generation
The process involves generating a pair of SSH key files containing a private key and a public key. The private key must be kept only on the user's computer; the public key will be distributed to the remote servers. Users must pay particular attention not to lose the private key. A lost private key cannot be replicated; therefore, the user cannot access the remote server until a new key pair is generated and the public key is redistributed."
To create and save SSH key files from a shell or Terminal, the ssh-keygen command is used; see the following example:
test@demo:~$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/test/.ssh/id_rsa):
Directory created '/home/test/.ssh'.
Enter passphrase (empty for no passphrase):
The keys are saved in a default location ($HOME/.ssh/id_rsa) or, if one was specified, with a different name. The public key has the .pub suffix.
The passphrase is a local password to further protect the private key and is never sent to the remote server. If a private key is stolen, it is useless without the passphrase. An empty passphrase is strongly discouraged.
Use the command man ssh-keygen for more information.
Further references
More detailed instructions can be found in Jump Hosts -- Passing Through a Gateway, with man ssh and man ssh_config under Linux or by searching Google for 'ssh jump host'.
Windows openssh
From Windows 10 1803 onwards, openssh is available as a command line. It can be started from cmd or powershell.exe. We suggest installing the new terminal from Microsoft: https://github.com/microsoft/terminal also available from Microsoft Store.
Windows PuTTY
On Windows 10/11, we recommend using the integrated openssh client.
PuTTY can use the jump host with its plink.exe utility. To configure the jump host:
- Once in a CMD shell, launch
plink.exe <fbk_login_name>@jump.fbk.eu, store the key, and ignore the error message: Fatal Error. - Load the access ssh key into Pageant.
Open a New Session in PuTTY. In Session, enter Host Name (or IP address) (<hostname>.fbk.eu) and Port (22) or of the destination host.

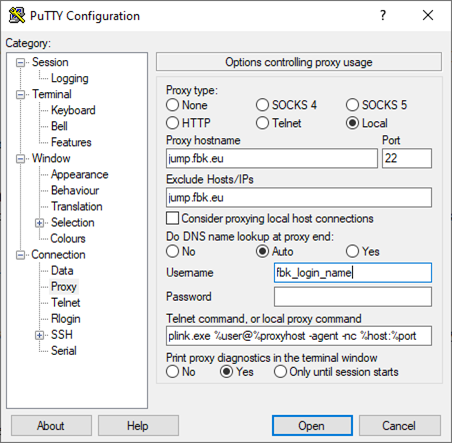
- Under Connection, select Proxy, under Proxy type select Local. Add jump.fbk.eu to both Proxy Hostname and Exclude Hosts/IPs.
- In the same Proxy screen, add your <fbk_login_name> as Username (the Password field is ignored);
- Delete the content of Telnet command, or local proxy command and replace it with:
plink.exe %user@%proxyhost -agent -nc %host:%port
%user is replaced by Username, %proxyhost by Proxy Hostname, %host by Host Name (or IP address).
Full description of PuTTY.
SSH KEY GENERATION WITH Putty
For the generation and use of ssh keys in PuTTY under Windows: Use SSH Keys With PuTTY On Windows or https://www.ssh.com/ssh/putty/windows/puttygen.
The public key used by the Jump Host must be in SSH format. In PuTTYgen, copy the content of the 'Public key for pasting into OpenSSH authorized keys file' and save it on a file; this is the public key.
Windows WinSCP
WinSCP can import and use PuTTY configurations.
Each PuTTY JumpHost configuration is transformed upon import into an scp over JumpHost configuration with WinSCP.
As per PuTTY, the SSH key must first be entered into Pageant.
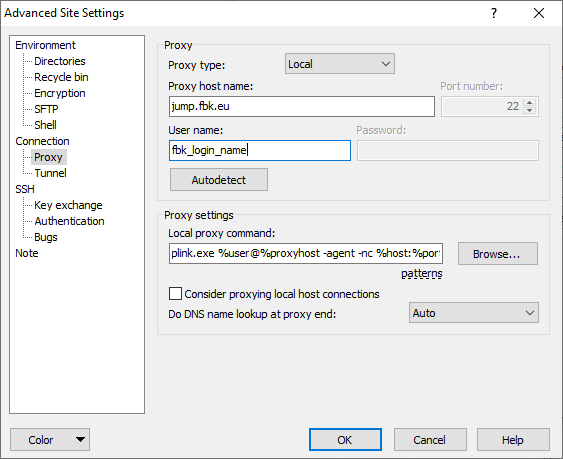
The JumpHost manual configuration can be found in Advanced Site Settings, section Connection->Proxy
Windows MobaxTerm
On Windows 10 and Windows 11, we recommend using the integrated openssh client.
MobaXterm can use a jump host to connect.
Once a session is created, in Basic SSH Settings, you must enter <hostname>.fbk.eu as Remote host, enable Specify Username and add <fbk_login_name>. In Advanced SSH Settings, enable Use private key and choose the relevant SSH key (openssh format).

Finally in Network Settings define jump.fbk.eu as Gateway SSH server, specify <fbk_login_name> as User, enable Use private key and choose the relevant SSH key (openssh format).

SSH key generation with MOBAXTERM
To generate and use SSH keys in MobaxTerm see the official documentation: https://mobaxterm.mobatek.net/documentation.html#6_3_2
Error messages
Common error messages are:
<login_name>@jump.fbk.eu: Permission denied (publickey).
The private SSH key sent does not match the public key registered for the jump host. Check the command.Received disconnect from 217.77.82.20 port 22:2: Too many authentication failures.
All private SSH keys found in$HOME/.ssh/are sent to the server one at a time. To prevent a key-based attack, after 3 attempts, the jump host denies access. Use theIdentitiesOnlyandIdentityFiledirectives (seeman ssh_config) or the alternative configuration file described above.Login prompt from internal hostThe public SSH key registered for the jump host is not present in$HOME/.ssh/authorized_keyson the internal server.
For different error messages, send a notification to [email protected].
BASTION
Remote access to internal workstations is available without the need for any VPN via browser by connecting to bastion.fbk.eu with your FBK credentials.
The supported protocol types are: SSH, VNC, or RDP.
To access the service, send an email to [email protected] with the subject 'Add new connection on Bastion' and specifying the following information:
- Protocol type: VNC, SSH, or RDP
- Name of the workstation you want to connect to
- vncserver listening port previously configured by the user (only for VNC connections)
Once the request is processed, the connection to the workstation will be made available to the requester; it will then be visible on bastion.fbk.eu
VPN connection request
The methods to access the FBK trusted network described above cover most of the needs of FBK users.
If the use of a VPN connection is necessary, the user must send an email to [email protected] with the subject 'VPN enablement request', specifying:
- why they want to use the VPN connection
- whether the computer from which they are opening the connection is self-managed or managed by FBK
frequently asked questions
F.A.Q.
How do I connect to the FBK network from home/university?
To connect to the FBK trusted network, in most cases, you can use BASTION and JUMPHOST. For specific needs, send an email to [email protected].